

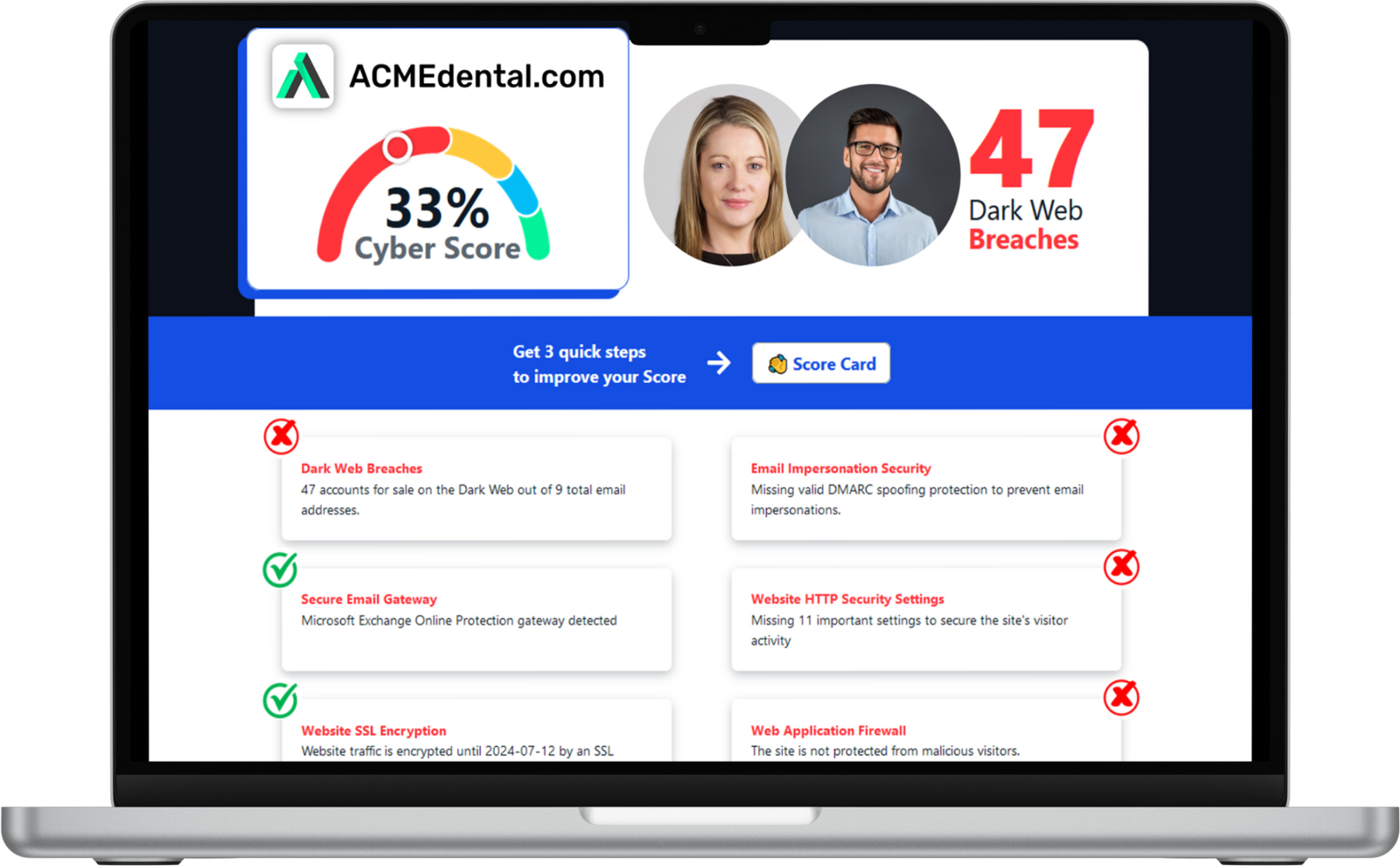
Think you're secure? Get your Cyber Security Score!
Get it in 30 seconds!
Enter Your Website URL to Get Your Cyber Score Right Now:
Your Trusted Partner for Proactive, Reliable, and Affordable Outsourced IT Support in Greater Grand Rapids
At West Michigan Technology Services (WMTS), we provide outsourced IT support designed to help your business operate smoothly, securely, and efficiently. Whether you’re looking to outsource your IT department, strengthen your cybersecurity posture, need an IT team to set up your 3CX Business Phone System, or get managed IT services in Grand Rapids, our team delivers expert support tailored to your needs.
From remote IT support to on-site troubleshooting, we handle every aspect of your technology so you can focus on running your business — not fixing IT issues.

WMTS Podcast Studio
Our Latest Episodes
Discover the latest episodes where we break down real-world IT challenges for West Michigan companies, share expert guidance on managed IT services, cybersecurity, and vCIO strategy, and explore emerging tech trends to help your business stay secure, efficient, and future-ready.
Marketing Wins, Studio Builds & Cyber Simulations | Bourbon 30 Podcast
Phishing Attacks, Spam Chaos & Security Wins | Bourbon 30 Podcast | West Michigan Tech Services
Law Meets IT Over Bourbon | Stacy Van Dyken on Bourbon 30 Podcast | West Michigan Tech Services
We’re Too Busy Fixing IT to Brag About It...
Our Clients Share Their Experience With Our Trusted Managed IT Services in Greater Grand Rapids and Across Michigan
Think you're secure? Get your Cyber Security Score!
Get it in 30 seconds!
Enter Your Website URL to Get Your Cyber Score Right Now:

Think you're secure? Get your Cyber Security Score!
Get it in 30 seconds!
Enter Your Website URL to Get Your Cyber Score Right Now:
Stay Secure. Stay Operational. We've Got Your Back.
Cybersecurity threats are increasing, but managing IT doesn’t have to be stressful. West Michigan Technology Services provides outsourced IT support in Grand Rapids with a security-first approach, keeping your business protected, productive, and prepared.
When You Have Security-First IT
Proactive Protection, No Surprises
Our outsourced IT support in Grand Rapids focuses on prevention, monitoring threats, applying updates, and stopping issues before they disrupt your business.
Real-World Solutions, Not Scare Tactics
No fear-based selling. We deliver managed and outsourced IT support aligned with your goals, budget, and risk level.
Seamless Security, Zero Hassles
Strong security shouldn’t slow you down. Our solutions run in the background, keeping you safe without interrupting your workday.
Trustworthy Advice, No Tech Jargon
We make cybersecurity easy to understand. No confusing buzzwords, just straight talk and real solutions that actually work for you.
When You Don’t Have Security-First IT
Outdated Systems, Easy Targets
Missed updates and unmanaged systems make businesses easy targets.
Fear-Driven Overcomplication
Some IT companies push unnecessary tools just to make a sale. We focus on what you actually need, not what they want to sell.
Inconvenient Security Roadblocks
Ever had security that makes work harder? That’s a fail. Security should protect you, not slow you down at every turn.
Confusing Advice, Costly Mistakes
If your IT provider leaves you guessing about security, you could be one misstep away from a costly data breach.
The More You Know...
Our blog shares practical guidance, expert takes, and real-world lessons drawn from the front lines of IT services. Stay informed, stay protected, and make smarter decisions for your business.

6 Habits That Quietly Decide If Hackers Win or Lose
Most cyberattacks don’t start with a mastermind hacker running lines of code in some movie-style lair. They start with something small.
A sticky note with a password written on it.
A rushed click on a link that “looked fine.”
A laptop left unlocked while its owner grabs a coffee.
One moment like that can undo every dollar your business has invested in security. And the scary part? Hackers count on these moments. They know technology is only half the battle the other half is human behavior.
The good news? The same way one bad habit can open the door, one good habit can keep it shut. And if your whole team follows these six, you’ll be miles ahead of the companies that don’t.
1. Stop Writing Down Passwords
Passwords are like house keys they only work if you keep them safe. The moment yours ends up on a Post-it or in an unprotected file, it’s like leaving a copy of your front door key under the welcome mat.
Hackers know this. Anyone who sees that note, even for a second, can access your accounts.
Instead:
Memorize your passwords or use a reputable password manager.
Don’t reuse passwords between accounts.
Keep them out of email, chat, and shared documents.
2. Think Before You Click
Most phishing attacks don’t look like scams at first glance. They’re designed to look familiar, urgent, and legitimate; a shipping notice, a client request, a security alert.
That’s why hackers love busy people. The more distracted you are, the more likely you’ll click without checking.
Before you click:
Hover over the link to see the real destination.
Check the sender’s email address for typos or weird domains.
If it feels off, confirm through a separate channel before acting.
3. Report Weird Stuff Right Away
This is one of the simplest, most effective defenses… and one of the most ignored.
If something looks suspicious; an odd email, a strange pop-up, your computer suddenly slowing down tell your IT team now. Don’t wait until after lunch. Don’t assume “it’s probably nothing.”
Early reports can turn a potential breach into a quick fix. Delays give threats time to spread.
4. Don’t Plug in Random USB Drives
That free flash drive from a trade show? It might come with malware as a bonus. Dropped-in-the-parking-lot USB drives are a known hacker tactic.. they rely on curiosity or convenience to get you to plug them in.
The second you do, you’ve bypassed most of your company’s digital defenses.
Safer approach: Only use devices issued or approved by your company. If you don’t know where it came from, don’t connect it.
5. Keep Work Devices for Work Only
It’s tempting to stream a movie, shop online, or install a personal app on your work laptop. But every non-work activity increases your exposure to malicious websites, shady downloads, and compromised accounts.
When you use work tech for personal use, you’re mixing trusted business systems with unverified sources.. and hackers love that.
Draw a hard line: work devices are for work tasks, personal devices are for personal use.
6. Lock Your Screen Every Time You Walk Away
Even a quick trip to the break room is enough time for someone to access your computer. It doesn’t have to be malicious.. even a curious glance at the wrong file can cause problems.
Make it second nature to lock your screen whenever you step away. Learn the keyboard shortcut for your system and use it without thinking.
The Bottom Line
Technology can stop a lot of threats, but it can’t fix bad habits. Every employee is part of the security team whether it’s in their job description or not.
The companies that avoid costly breaches aren’t just the ones with the best firewalls; they’re the ones whose people build good security habits into their daily routine.
If you’re a client, these habits are reinforced in our training and systems. If you’re not, this list is your starting point. Because in the end, the difference between stopping an attack and suffering through one often comes down to small choices made in seconds.
West Michigan Technology Services
is Your Trusted Grand Rapids IT Support, Cybersecurity, and 3CX Business Phone System Company
Reliable IT Outsourcing Services That Keep You Connected and Secure
Your technology should empower your team, not slow it down. With WMTS, you gain access to outsourced IT services designed for growing Michigan businesses. Our managed IT outsourcing model ensures your systems are monitored 24/7, keeping downtime to a minimum and productivity high.
We provide fully managed IT support and maintenance to keep your infrastructure running efficiently. Our team also delivers comprehensive cybersecurity protection and data recovery solutions to safeguard your business from digital threats and unexpected data loss.
Through our cloud management and remote monitoring services, we help you stay connected and secure, no matter where your team operates. In addition, our helpdesk and user support outsourcing ensures that your employees always have access to fast, friendly technical assistance when they need it most.
For businesses that rely on modern communication, we also handle 3CX business phone system setup and management, helping you streamline collaboration and improve call quality.
As your trusted IT partner, WMTS delivers enterprise-level technology and support at a cost that fits small and midsize business budgets. Learn more about our company and team on our About page.
YOUR DATA AND BUSINESS SAFETY COME FIRST WITH US
The West Michigan Technology Services Approach
Relationships Built to Last
We don’t just fix IT issues—we provide IT support solutions and build long-term partnerships. Our first clients are still with us because we prioritize trust, reliability, and IT services that truly support their business.
No-Nonsense IT
Tech should be simple, not a headache. With our IT outsourcing solutions, we cut through the jargon, offer clear solutions, and ensure you get exactly what you need—no upselling, no unnecessary extras, just results.
vCIO Services That Deliver
We go beyond fixing problems—we help you plan for the future. Our vCIO services align your technology with your business goals, ensuring smart, strategic decisions that drive success.
Fun, But Always Professional
We love what we do, and it shows. Our team delivers outsourced IT support services and IT Solutions with a friendly, approachable style—keeping your business running strong without the IT stress.
Our Core Values
At the core of everything we do is a simple belief: IT should be honest, helpful, and human. From day one, we've focused on earning trust, building long-term relationships, and providing no-nonsense support that actually helps businesses grow.
WMTS Core Values
Our core values are the non-negotiable principles that guide everything we do here at WMTS. We expect our team to live by these values in all interactions, and we are confident that our clients will see these values in action
Integrity
Integrity means sticking to strong morals even when tempted to cut corners when no one is looking. You can count on us to always be honest and make recommendations that truly benefit you, not just make a sale. Trust is at the foundation of our relationships. We may not have yours just yet, but we will earn it. (Integrity – Upholding honesty and ethicality in everything we do.)
Gratitude
There are many other MSP options around, and we’re deeply grateful whenever someone chooses us. We’ll do our best to show our appreciation through top-notch service and support. (Gratitude –Genuine appreciation for every client who chooses us.)
Humility
Technology can be confusing and frustrating! We’ll always approach your issues with patience and understanding. We aim to provide the kind caring service we would want ourselves. (Humility -Meeting every client with patience and care.)
Loyalty
We believe in building long-term relationships founded on trust. We’ll stay loyal to our clients as long as it doesn’t compromise our integrity. (Loyalty – Building trust through long-term, honest, & ethical relationships.)
Growth
This business moves fast! Learning and improving daily is crucial to keep up. We prioritize constant professional and personal growth so we can deliver our best to you. (Growth –Constantly improving to better serve you.)
Our core values define our business. We uphold integrity, express gratitude, lead with humility, embrace loyalty, and pursue growth each day. This guides every single one of our interactions and services. Let us know if you have any questions! We look forward to working with you.
Ready for IT Support That Actually Cares About You?
Here are Three Ways We Can Help:
01
Find out how secure you really are
02
Sign Up For Our Cybersecurity newsletter
Learn How A Security-First IT Strategy Benefits Your Company:
03
ask us anything
Have a Question About Cybersecurity? We Have The Answers You're Looking For.
We’re happy to advise on anything cybersecurity-related, with no strings attached.
Call (616) 310-6966 or email [email protected]
Frequently Asked Questions
What is outsourced IT support and how can it benefit my business?
Outsourced IT support allows your business to delegate IT management to experts like WMTS. This ensures your systems run smoothly, securely, and efficiently while reducing costs compared to hiring a full in-house IT team.
What IT outsourcing services does WMTS offer?
WMTS provides comprehensive IT outsourcing services, including managed IT services, cybersecurity, cloud management, helpdesk support, and 3CX business phone system setup. Our solutions are tailored for businesses across Grand Rapids and West Michigan.
How does WMTS ensure 24/7 IT support?
We use proactive monitoring, remote management tools, and a dedicated support team to detect and resolve issues before they impact your business. Whether it’s on-site or remote troubleshooting, we’re available whenever you need assistance.
What makes WMTS different from other IT service providers?
WMTS combines local expertise, a security-first approach, and scalable managed IT outsourcing solutions. Our team treats your IT like our own, providing personalized, reliable, and cost-effective support for Michigan businesses.
Can WMTS handle cybersecurity and data protection for my company?
Yes! WMTS provides robust cybersecurity services, including firewalls, phishing protection, and data recovery solutions, ensuring your business stays protected from digital threats while maintaining compliance with industry standards.
Smarter IT, Less Stress, and More Success
Get IT support and IT solutions that go beyond quick fixes. We deliver proactive solutions and long-term partnerships to keep your business running smoothly. Serving clients in Greater Grand Rapids and nearby areas, and remotely across Michigan. We’re here to solve your IT challenges and secure your business future.
Call (616) 310-6966 today or hit the button below to get started. We’re here to make IT work for you!















